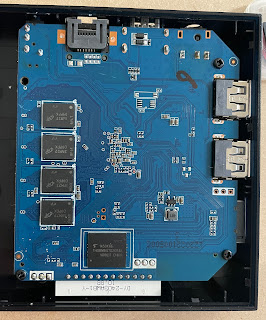
This is a story of failure, but I thought it worthwhile to share it. There are reports that some of the cheap (~$40) Android TV boxes advertised on sites like AliExpress, can be encouraged to boot Armbian linux and so can be used as a Linux server for very little money. A common one is called T95 so I ordered a 4GB ram version. Here's the board unboxed:
There is a push button switch cleverly mounted behind the 3.5mm "AV" socket so you can poke a toothpick through it to press it during power on to trigger an attempt to boot from the SD card.
The board I got is labelled: “H616-T95MAX-AXP313A-V3.0”
I have downloaded numerous promising linux images but each time I try it just sits silently during the attempted boot.
There are three pins between the SD card and one of the USB ports that are the serial console port. I soldered a header on to these and found that it sends debug messages during Android boot at 115200 8-N-1. Here's a snippet:
HELLO! SBOOT is starting
U-Boot 2018.05 (Jul 29 2022 - 19:51:27 +0800) Allwinner Technology
[01.301]CPU: Allwinner Family
[01.304]Model: sun50iw9
I2C: ready
[01.308]DRAM: 2 GiB
[01.311]Relocation Offset is: 75ec5000
[01.351]secure enable bit: 1
[01.354]pmu_axp152_probe pmic_bus_read fail
[01.358]PMU: AXP1530
[01.364]CPU=1008 MHz,PLL6=600 Mhz,AHB=200 Mhz, APB1=100Mhz MBus=400Mhz
[01.372]drv_disp_init
[01.401]__clk_enable: clk is null.
[01.407]drv_disp_init finish
[01.409]gic: sec monitor mode
[01.437]flash init start
[01.439]workmode = 0,storage type = 2
[01.443]MMC: 2
[01.444]get mem for descripter OK !
[01.453]get sdc2 sdc_boot0_sup_1v8 fail.
[01.457]io is 1.8V
Interesting that although I paid for, and the case is labelled, 4GB, the console says it's 2GB.
The box works quite well running Android. The Google Play store works (although you must log in with a Google Account). Installing UserLAnd gives you a pretty good linux command line running on top of Android. The supplied Android has been modified in various ways including a "root" switch.
Malware
There are reports of Android TV boxes coming from China with malware pre-installed. Once I had a command line and had switched the root switch on I was able to see that this box has the telltale files they mention.
Scammy Play Store apps
I don't use Android very much but playing with this box led me to search for and install some apps from the Play store for things like BusyBox. My goodness! there are some truely evil apps that Google has let in to the Play store. One popular BusyBox insisted on playing a full screen video of a game at every use, another app demanded accessibility privileges which Android explained would give it full access to all keystrokes typed.
Conclusion
To be fair, the Armbian site makes it clear that boxes like this can't be supported. The H616 chip is pretty new and even if I got it working it's likely that vital things like Wifi might not work. Searching for bootable linux images is a bit of a mine field with several links being blocked by my browser's malware blocker.
Oh, and of course this story is an example of Betteridge's law of headlines.


3 comments:
(EDIT:deleted previous as trying to fix display name - now reinstated below)
Thanks for posting. Useful to learn from other's mistakes (if indeed this was a mistake). A valuable lesson in how easily malware can proliferate.
Tx 9 pro power ase na
Post a Comment